Troubleshooting Jira Account Configuration Errors in Calibo Accelerate
When configuring Jira account connection details in Calibo Accelerate, administrators may encounter errors related to network connectivity, secrets management in AWS Secrets Manager or Azure Key Vault, or Calibo Accelerate Orchestrator Agent.
This article provides a consolidated reference to the most common Jira connection configuration errors, their causes, and recommended resolutions.
Atlassian Server Connectivity Errors
Error
The Atlassian server is not reachable. Check your network connection and verify the URL.
Possible Cause
The Jira instance URL entered in the configuration is incorrect.

Resolution
-
Verify and update the Jira instance URL (for example, https://yourcompany.atlassian.net).

Note:
The URL may vary depending on your company’s setup.
-
Check for typos (such as .net vs .ne or extra characters).
Tip:
Always copy-paste the URL from your Jira instance to avoid manual entry errors.
Invalid Credentials Entered Directly in Platform
Error
Connection details are incorrect, or you do not have the necessary permissions to access this Jira instance, or your Atlassian subscription has expired.
Possible Cause
This error may occur when Jira credentials are entered directly in Calibo Accelerate (without using AWS Secrets Manager or Azure Key Vault) and one or both values are invalid. Common reasons include:
-
The Username or API Token is incorrect or invalid.
-
The Jira user account does not have sufficient permissions to access the specified Jira instance.
-
The Atlassian subscription for the account or instance has expired or is inactive.

Resolution
-
Verify the Username and API Token
-
Ensure the username is correctly entered and matches the Jira account that generated the token.
-
Ensure the API token entered is valid, not expired, and correctly copied.
-
-
Check User Permissions
-
Confirm that the Jira user has sufficient access rights.
-
The user should have at least read and write permissions on the targeted Jira space or project.
-
-
Validate Atlassian Subscription
-
Confirm that the organization’s Atlassian subscription is active.
-
If issues are found, contact Atlassian support to resolve subscription problems.
-
Tip:
-
Always ensure the API token belongs to the same user specified in the Username field.
-
Avoid using expired or revoked tokens.
AWS Secrets Manager-Related Errors
These errors indicate issues with the Jira credentials stored in AWS Secrets Manager. The configuration expects valid username and password keys inside the specified secret. If any of them are missing, incorrect, or the secret itself is not found, you will encounter the errors listed below.
Username Key Not Found
Error
The key <username key> was not found in the secret <secret name>.
Possible Cause
The username key specified in the configuration does not exist in the selected AWS Secrets Manager secret.
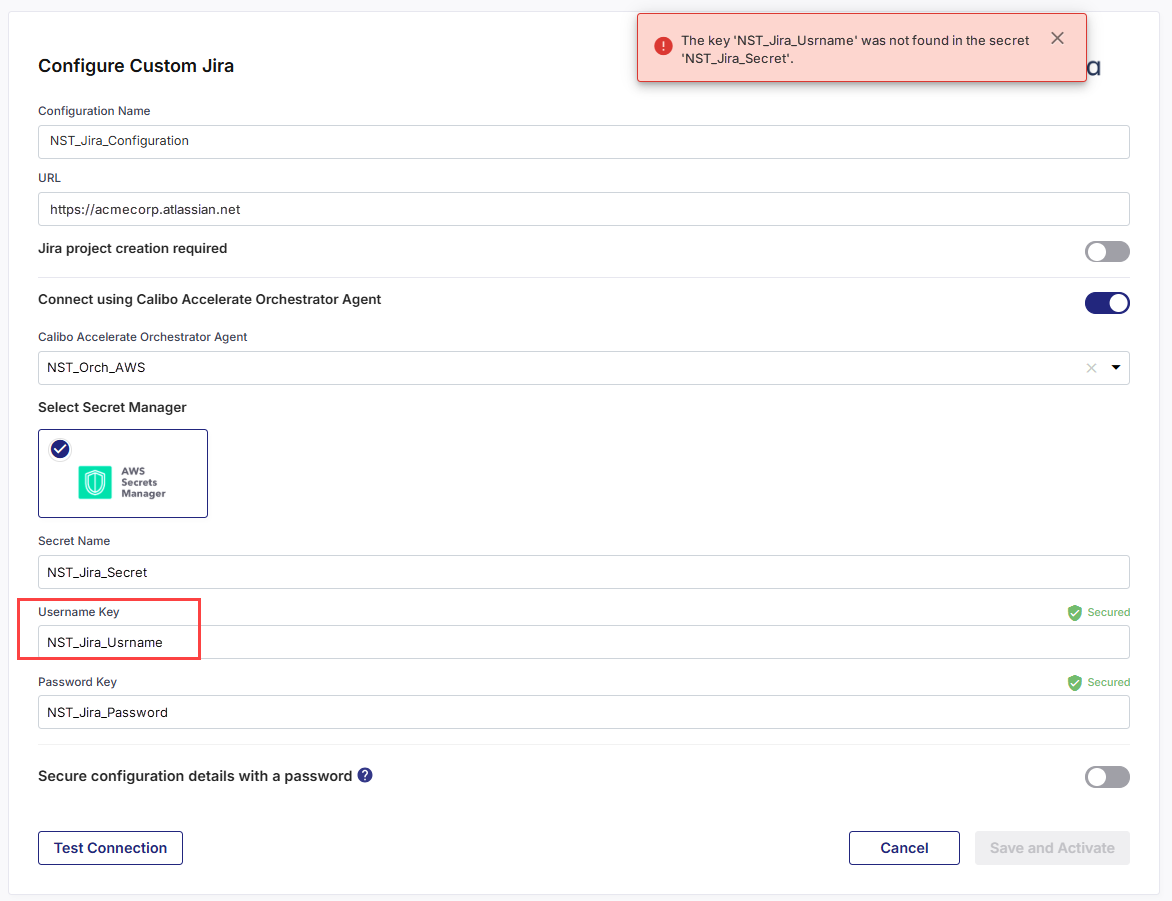
In this example, you are using a Calibo Accelerate Orchestrator Agent to programmatically resolve the Jira credentials stored in AWS Secrets Manager within your private network and establish communication with Jira. The agent attempts to fetch the username key NST_Jira_Usrname, but does not find it in the secret NST_Jira_Secret. In this case, NST_Jira_Usrname looks like a typo.
The same error may also occur even if no Orchestrator Agent is used. In this case, the platform directly looks for the configured username key in your selected AWS Secrets Manager. The error appears if the key is incorrectly configured in Calibo Accelerate or if the configured key does not exist the secret in AWS Secrets Manager.
Resolution
-
Sign in to AWS Secrets Manager.
-
Locate the secret NST_Jira_Secret.
-
Verify that the correct username key exists (case-sensitive).
-
Update the Jira configuration in Calibo Accelerate with the correct key name.
Tip:
Always use exact key names; avoid typos, extra spaces, or unnecessary suffixes.
Password Key Not Found
Error
The key <password key> was not found in the secret <secret name>.
Possible Cause
The password key specified in the configuration does not exist in the selected AWS Secrets Manager secret.
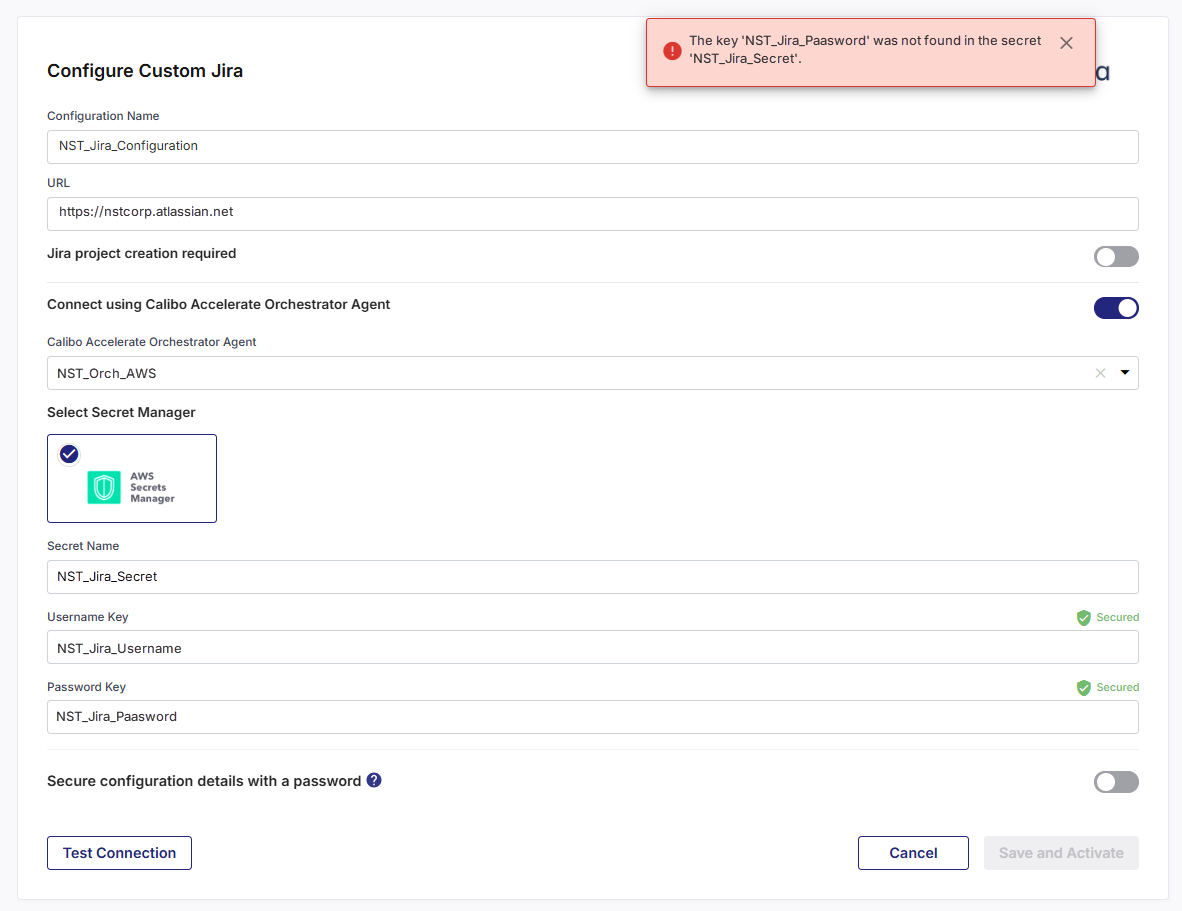
When using a Calibo Accelerate Orchestrator Agent, the agent programmatically retrieves Jira credentials from AWS Secrets Manager to establish communication with Jira. In this case, the agent attempts to fetch the password key NST_Jira_Paasword but does not find it in the secret NST_Jira_Secret. In this case, NST_Jira_Paasword looks like a typo.
The same error may also occur even if no Orchestrator Agent is used. In this case, the platform directly looks for the configured password key in your selected AWS Secrets Manager. The error appears if the key is incorrectly configured in Calibo Accelerate or if the configured key does not exist the secret in AWS Secrets Manager.
Tip:
Both <username key> and <password key> must exist in the secret.
Secret Not Found
Error
The secret <secret name> was not found in AWS Secrets Manager.
Possible Cause
The secret name entered in the Jira configuration does not exist in AWS or is in a different region.

With Orchestrator Agent
If you are using a Calibo Accelerate Orchestrator Agent, the agent looks for the specified secret in the configured AWS Secrets Manager to programmatically fetch the Jira credentials. This error occurs when the agent does not find the secret (in the example screenshot, NST_Jira_Secret) in the expected location, either because the wrong secret name was configured in Calibo Accelerate or because the secret was removed or renamed in AWS.
Without Orchestrator Agent
The same error may occur even if no Orchestrator Agent is used. In this case, the platform itself tries to fetch the secret from AWS Secrets Manager but cannot locate it, either because the wrong secret name was configured in Calibo Accelerate or because the secret was removed or renamed in AWS.
Resolution
-
Verify the secret name in AWS Secrets Manager (case-sensitive).
-
Replace the incorrect secret name in the configuration.
-
Use copy-paste to avoid typos, spacing issues, or capitalization errors.
Tip:
Double-check for typos, extra spaces, or capitalization errors.
Azure Key Vault-Related Errors
These errors indicate issues with the Jira credentials stored in Azure Key Vault. The configuration expects valid username and password secrets inside the specified vault. If the vault is not found, or if the required secrets are missing, misconfigured, or inaccessible due to permission issues, you will encounter the errors listed below.
Vault Not Found
Error
The vault <vault name> was not found in Azure Key Vault.
Possible Cause
-
The vault name specified in the Jira configuration does not exist.
-
The vault may be in a different Azure subscription, environment, or region.
-
There may be a typo, spacing, or capitalization error in the vault name.

With Orchestrator Agent
When using a Calibo Accelerate Orchestrator Agent, the agent attempts to programmatically resolve Jira credentials from Azure Key Vault. This error occurs when the agent looks for the vault specified in the Jira configuration but does not find it in the configured Azure environment.
Without Orchestrator Agent
The same error may also occur without an Orchestrator Agent. In this case, the platform directly attempts to access the specified vault in Azure Key Vault. If the vault is not present, incorrectly specified, or inaccessible, the error is triggered.
Resolution
-
Sign in to the Azure Portal and verify the vault name.
-
Ensure that the vault is in the correct subscription / region.
-
Replace the vault name in the Jira configuration with the correct one.
Tip: Vault names are case-sensitive. Copy the correct vault name from Azure Portal.
Username Secret Not Found
Error
The secret <username secret> was not found in the vault <vault name>.
Possible Cause
-
The username secret specified in the configuration does not exist in the specified vault.
-
The secret may have been renamed or deleted.

With Orchestrator Agent
When using a Calibo Accelerate Orchestrator Agent, the agent programmatically retrieves the Jira credentials stored in Azure Key Vault. This error occurs when the agent looks for the specified username secret in the configured vault but does not find it.
Without Orchestrator Agent
The same error may occur even if no Orchestrator Agent is used. In this case, the platform itself attempts to fetch the secret from Azure Key Vault. The error appears if the username secret is incorrectly specified in Calibo Accelerate or has been removed from the vault.
Resolution
-
Sign in to the Azure Portal.
-
Check whether the username secret specified in the Jira connection configuration exists inside the specified vault.
-
Update the configuration in Calibo Accelerate with the correct secret name.
-
Verify that the user running the configuration has sufficient permissions.
Tip:
Always use exact secret names; avoid typos, extra spaces, or unnecessary suffixes.
Password Secret Not Found
Error
The secret <password secret> was not found in the vault <vault name>.
Possible Cause
-
The password secret specified in the configuration does not exist in the specified vault.
-
The secret may have been deleted or incorrectly named.
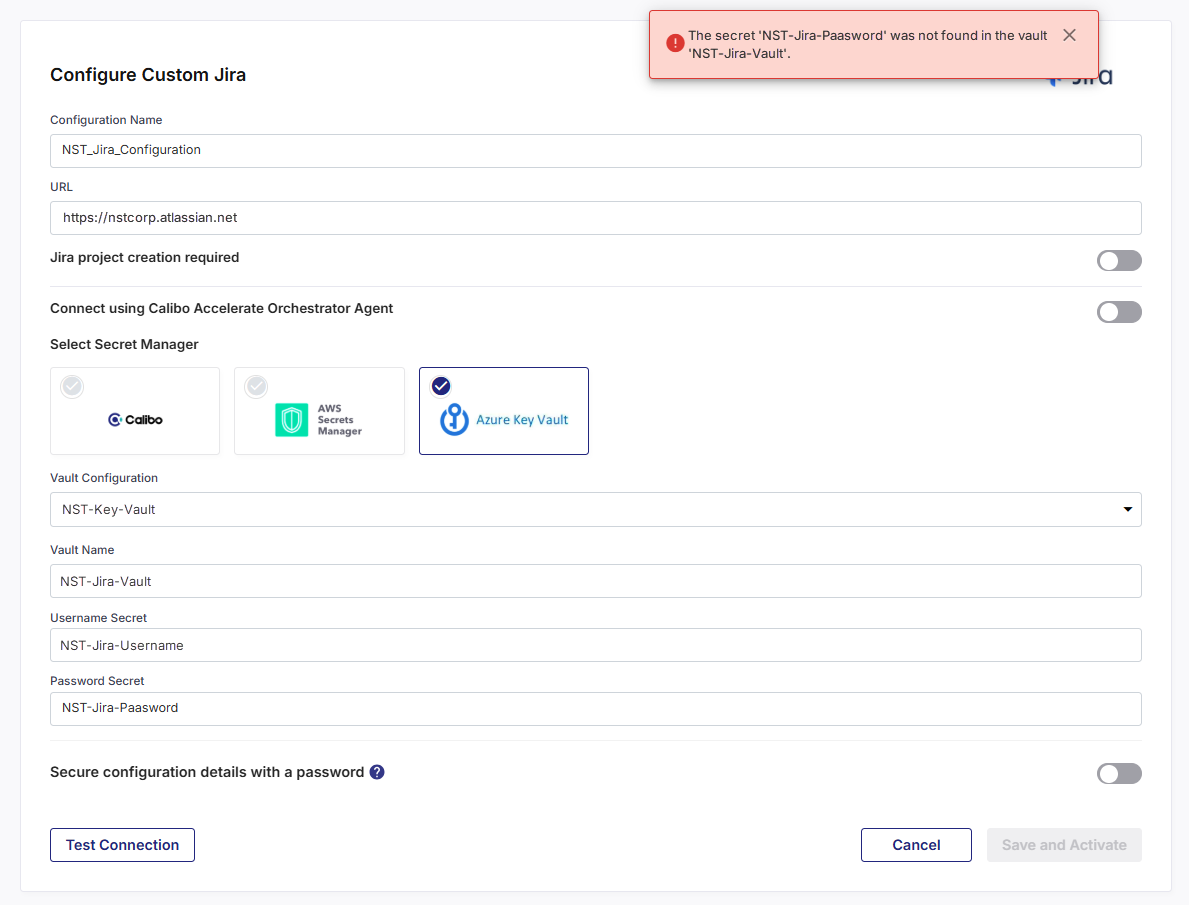
With Orchestrator Agent
When using a Calibo Accelerate Orchestrator Agent, the agent programmatically fetches Jira credentials from Azure Key Vault. The error appears when the agent looks for the specified password secret in the configured vault but does not find it.
Without Orchestrator Agent
The same error may also occur without an Orchestrator Agent. In this case, the platform directly queries Azure Key Vault for the password secret. If the secret is misconfigured in Calibo Accelerate or has been removed from the vault, the error will be triggered.
Resolution
-
Sign in to the Azure Portal.
-
Check whether the password secret specified in the Jira connection configuration exists inside the specified vault.
-
Update the Jira configuration with the correct secret name.
-
Ensure the user has Get/List access rights to the secret in the vault.
Tip: Copy the correct secret name from Azure Portal.
Orchestrator Agent Unavailable
Error
Calibo Accelerate Orchestrator Agent <agent name> is currently unavailable. Please try again later.
Possible Cause
-
The designated Orchestrator Agent is offline or unresponsive.
-
Network misconfiguration or agent-component failure is preventing communication.
Resolution
-
Verify Agent Deployment
-Confirm that the Orchestrator Agent microservices are correctly installed in your environment ( in AWS EKS, or Azure AKS). If required, reinstall or restart the agent.
-
Check Health Status
-Navigate to Configuration > Platform Setup > Calibo Accelerate Orchestrator Agents in the Calibo platform.
-Verify the Provisioning Status, Last Heartbeat Status, and Test Connection metrics to ensure the agent is responsive.
-
Ensure Service Availability
-Make sure necessary networking (for example, ingress controllers, PrivateLink endpoints, TLS paths) are correctly configured and operational.
-Ensure the agent can receive REST API calls from Calibo Accelerate and connect to your secrets storage.
-
Switch Agents If Needed
-If you have multiple agent instances, select a different active one in the platform dropdown during configuration. The agent you select must have the required access to the secrets management tool where you store Jira credentials.
Tip: Monitoring agent's health and availability ensures uninterrupted integration and secure credential access.